Supporting Documents for Cybersecurity First Principles
As a companion to the book, here are some historical reference documents that might be useful for you:
- Agile Manifesto
- Bayes Success Stories (summarized from Sharon McGrayne's Book, The Theory That Would Not Die)
- Cybersecurity Canon Hall of Fame Books referenced in this book
- Kindervag's Nine (Zero Trust) Rules
- Research Summary on Why Heat Maps are Poor Vehicles for Conveying Risk
- Timelines
- Cybersecurity Historical Timeline
- Chaos Engineering Historical Timeline
- Encryption Historical Timeline
- Equifax Hack Timeline
- Identity and Authentication Historical Timeline
- Red Team, Blue Team Historical Timeline
- RSA Security Hack Timeline
- SDP (Software Defined Perimeter) Historical Timeline
Haven't read the book yet? You can order it from Amazon here.
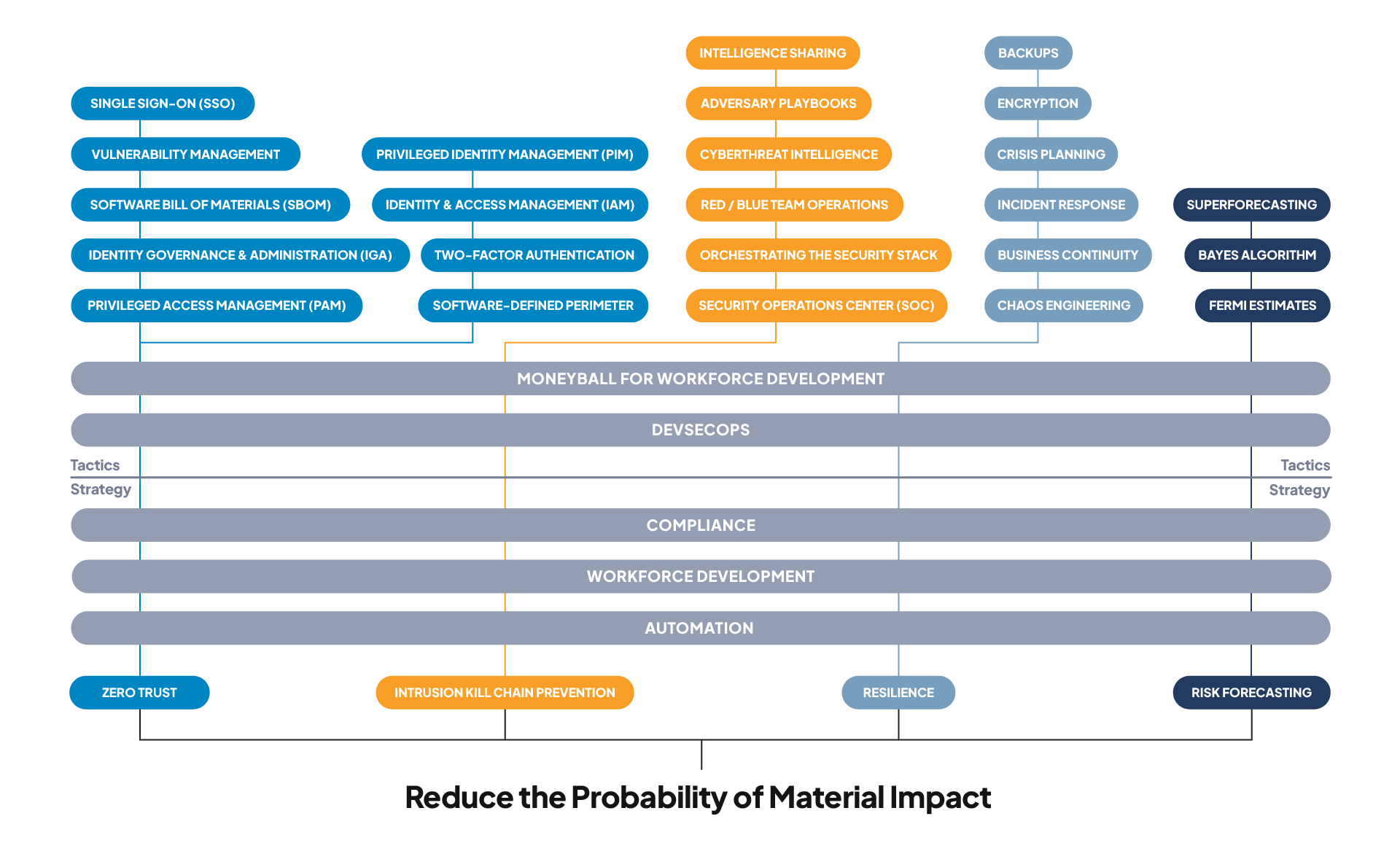
Road Map for Cybersecurity First Principles
This book covers a lot of material. The diagram below is the road map that you can use to accompany the book. Read it from the bottom up.
The first box is the foundation and absolute cybersecurity first principle (Chapter 2).
The next two rows are the follow-on first-principle strategies that you might use to pursue the ultimate first principle: zero trust (Chapter 4), intrusion kill chain prevention (Chapter 5), resilience (Chapter 6), risk forecasting (Chapter 7), and automation (Chapter 8).
The remaining boxes are the tactics you might use to pursue each strategy. They show up as sections within the chapters. The grey lines show the connections between the strategies and the tactics. note that the automation strategy and compliance tactic cut across everything. Chapter 8 tells you why.
Want a quick-hitting overview of the content covered? See our Cybersecurity First Principles course here.